Technology Threat Avoidance Theory (TTAT)
Acronym
- TTAT
Alternate name(s)
Main dependent construct(s)/factor(s)
Avoidance behavior
Emotion-focused coping
Main independent construct(s)/factor(s)
Risk tolerance, Social influence
Users’ perceived susceptibility and severity of malicious IT
A safeguarding measure's effectiveness, costs, and users' self-efficacy toward it
Concise description of theory
Technology Threat Avoidance Theory (TTAT) explains why and how individual IT users engage in threat avoidance behaviors. Unlike most studies that have examined IT security at the organizational level, TTAT provides a framework at the individual user level. The theory has been developed by Liang and Xue[1] by synthesizing the literature from diverse areas including psychology, health care, risk analysis, and information systems. The basic premise of TTAT is that when users perceive that an IT threat exists, they will be motivated to actively avoid an IT threat by taking a safeguarding measure if they believe that the threat can be avoided by following the safeguarding measure, or they will passively avoid the threat through emotion-focused coping if they perceive the threat not to be avoidable by any safeguarding measure available to them[1].
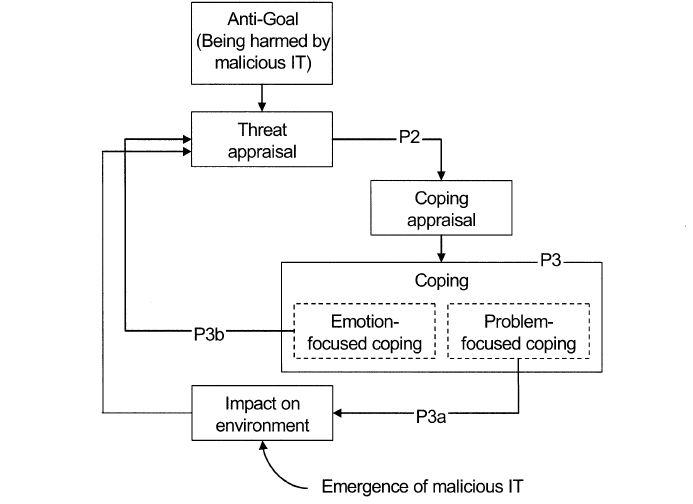
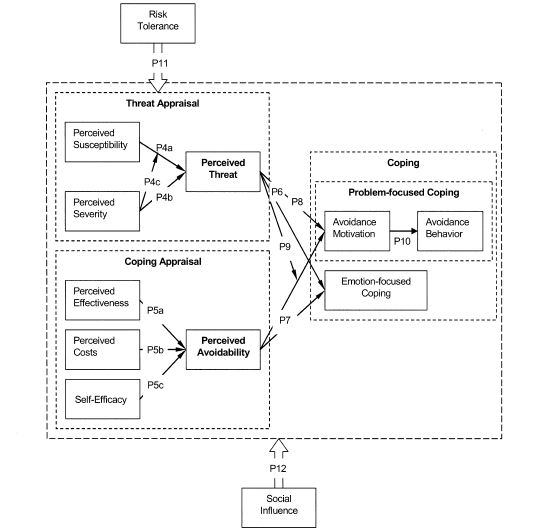
TTAT describes the processes and factors influencing individual users’ IT threat avoidance behavior. Drawing on cybernetic theory[2][3], TTAT posits that IT threat avoidance behavior can be represented by a cybernetic process in which users intend to enlarge the distance between their current security state and the undesired (unsafe) end state. With the help of coping theory[4][5], TTAT submits that users experience two cognitive processes, threat appraisal and coping appraisal. First, users appraise or assess the situation whether the IT threat exists and to what degree it exists. Then they decide what action they will take to avoid it—problem-focused coping and/or emotion-focused coping. TTAT identifies some key factors that explain user perception and motivation in this process. Integrating the literature of risk analysis[6][7] and health psychology[8][9][10], TTAT suggests that users’ threat perception is determined by the perceived probability of the threat's occurrence and the perceived severity of the threat's negative consequences. Based on prior research on health protective behavior[8][11] and self-efficacy[12][13], TTAT proposes that users conceive three factors to assess to what extent the threat can be made avoidable by taking a safeguarding measure—the effectiveness of the safeguarding measure, the costs of the measure, and users' self-efficacy of applying the measure.
TTAT makes significant contributions to the literature of IT security. This theory clarifies the approach-avoidance distinction which was neglected previously. TTAT posits that avoidance of a malicious threat is not similar to the acceptance of a safeguarding measure. This is based on the assumption that the avoidance and adoption behaviors are qualitatively different, hence the application of one theory in the other context may lead to inconsistent, even false findings. For example, when there exists the threat of spyware, studying adoption of anti-spyware may produce inconsistent findings. Moreover, the authors integrate a process theory view and a variance theory view of TTAT so that the theory can be tested by both process research and variance research. As process theory, TTAT describes IT users' avoidance behavior as a dynamic positive feedback loop[2]. The loop may start with the emergence of malicious IT in the environment. Once users become aware of that, they set being harmed by malicious IT as the anti-goal (undesired end state). If they perceive their current state is near the anti-goal, they will engage in coping mechanism to enlarge the discrepancy between the current state and the undesired end state. This threat avoidance behavior is said to continue until the discrepancy becomes too large that the threat disappears. The variance theory view of TTAT brings relevant variables to understand threat appraisal, coping appraisal, and coping. Furthermore, TTAT submits that users can apply both problem- and emotion-focused coping to reduce IT threats.
TTAT has the potential to assist IT executives and managers in raising security awareness and designing effective mechanisms to educate employees about IT threats, by understanding why users actively and passively respond to IT threats. The awareness should include the likelihood of getting attacked by malicious IT as well as the negative outcomes if the attack becomes successful. Besides, TTAT provides some prescriptive guidelines for IT practice.
Diagram/schematic of theory
Source: Liang, H., & Xue, Y. (2009, March). Avoidance of Information Technology Threats: A Theoretical Perspective. MIS Quarterly, 33(1), 71-90.
Originating author(s)
- Liang and Xue (2009)
Seminal articles
Liang, H., & Xue, Y. (2009, March). Avoidance of Information Technology Threats: A Theoretical Perspective. MIS Quarterly, 33(1), 71-90.
Originating area
- IS security
Level of analysis
- Individual
Links to WWW sites describing theory
Links from this theory to other theories
Protection motivation theory, General systems theory, Prospect theory, Self-efficacy, Social cognitive theory, Cybernetic theory, Coping theory
IS articles that use the theory
Arachchilage, N. A., & Love, S. (2014, September). Security awareness of computer users: A phishing threat avoidance perspective. Computers in Human Behavior, 38, 304-312.
Herath, T., Chen, R., Wang, J., Banjara, K., Wilbur, J., & Rao, H. R. (2014, January). Security services as coping mechanisms: an investigation into user intention to adopt an email authentication service. Information Systems Journal, 24(1), 61-84
Lai, F., Li, D., & Hsieh, C.-T. (2012, January). Fighting Identity Theft: The Coping Perspective. Decision Support Systems, 52(2), 353-363.
Liang, H., & Xue, Y. (2010, July). Understanding Security Behaviors in Personal Computer Usage: A Threat Avoidance Perspective. Journal of the Association for Information Systems, 11(7), 394-413.
Contributor(s)
- Anupriya Khan
Date last updated
- 28 Feb 2017
References
- ↑ 1.0 1.1 Liang, H., & Xue, Y. (2009, March). Avoidance of Information Technology Threats: A Theoretical Perspective. MIS Quarterly, 33(1), 71-90.
- ↑ 2.0 2.1 Carver, C. S., & Scheier, M. F. (1982). Control Theory: A Useful Conceptual Framework for Personality-Social, Clinical, and Health Psychology. Psychological Bulletin, 92(1), 111-135.
- ↑ Edwards, J. (1992). A Cybernetic Theory of Stress, Coping, and Weil-Being in Organizations. Academy of Management Review, 17(2), 238-274.
- ↑ Lazarus, R. (1966). Psychological Stress and the Coping Process. New York: McGraw-Hill.
- ↑ Lazarus, R., & Folkman, S. (1984). Stress, Coping, and Adaptation. New York: Springer-Verlag.
- ↑ Baskerville, R. (1991a). "Risk Analysis: An Interpretive Feasibility Tool in Justifying Information Systems Security". European Journal of Information Systems, 1(2), 121-130.
- ↑ Baskerville, R. (1991b). "Risk Analysis as a Source of Professional Knowledge". Computer & Security, 10(8), 749-764.
- ↑ 8.0 8.1 Janz, N. K., & Becker, M. H. (1984). The Health Belief Model: A Decade Later. Health Education Quarterly, 11(1), 1-45.
- ↑ Rogers, R. W. (1983). Cognitive and Physiological Process in Fear Appeals and Attitude Change: A Revised Theory of Protection Motivation. In R. Petty, Social Psychophysiology: A Source Book (pp. 153-176). New York: Guilford Press.
- ↑ Weinstein, N. D. (2000). Perceived Probability, Perceived Severity, and Health-Protective Behavior. Health Psychology, 19(1), 65-74.
- ↑ Maddus, J. E., & Rogers, R. W. (1983). Protection Motivation and Self-Efficacy : A Revised Theory of Fear Appeals and Attitude Change. Journal of Experimental Social Psychology, 19, 469-479.
- ↑ Bandura, A. (1982). Self-Efficacy Mechanism in Human Agency. American Psychologist, 37, 122-147.
- ↑ Compeau, D. R., & Higgins, C. A. (1995). Computer Self-Efficacy: Development of A Measure and Initial Test. MIS Quarterly, 19(2), 189-211.